14+ e1 vector
Easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where Oracle Communications Cloud Native Core Policy executes to compromise Oracle Communications Cloud Native Core Policy. Converting images to vector graphics makes it easier to resize them without any loss in quality that happens with JPEG or PNG images.

Civic Map London Higher
This Critical Patch Update contains 14 new security patches for Oracle PeopleSoft.

. Source Code TAR Ball. Theo WHO dựa trên phân tích đối với 44000 trường hợp mắc COVID-19 tại tỉnh Hồ Bắc khoảng 80 người mắc bệnh nhẹ 14 mắc bệnh nặng hơn như viêm phổi 5 nguy kịch và 2 trường hợp tử vong. A key point to remember is that in python arrayvector indices start at 0.
View the Project on GitHub broadinstitutepicard. This chapter specifies the meanings of expressions and the rules for their evaluation. Neurosurgery the official journal of the CNS publishes top research on clinical and experimental neurosurgery covering the latest developments in science technology and medicineThe journal attracts contributions from the most respected authorities in the field.
Electrocardiography is the process of producing an electrocardiogram ECG or EKG a recording of the hearts electrical activity. MicroeconomicsDistributionPersonal Income Wealth and Their Distributions G01. Indexing is the way to do these things.
For example maybe you want to plot column 1 vs column 2 or you want the integral of data between x 4 and x 6 but your vector covers 0 x 10. From 1950 to 1980 DDT was extensively used in agriculture more than 40000 tonnes each year worldwide and it has been. Electromagnetism is a branch of physics involving the study of the electromagnetic force a type of physical interaction that occurs between electrically charged particles.
With a wooden ruler you measure the length of a rectangular piece of sheet metal to be 12 mm. Time Slot Interchange TSI Digital Switches. It includes a wealth of information applicable to researchers and practicing neurosurgeons.
Visit Our Press Center. The Indian Space Research Organisation ISRO. USB Switches.
The supported version that is affected is 1140. Given two vectors A400i700j and B500i200j a find the magnitude of each vector. Macroeconomics and Monetary EconomicsMonetary Policy Central Banking and the Supply of Money and CreditMonetary Policy D22.
A set of command line tools in Java for manipulating high-throughput sequencing HTS data and formats such as SAMBAMCRAM and VCF. Change of address except Japan. Vector Attack Complex Privs Reqd User Interact Scope Confid-entiality Inte-grity Avail-.
Write each vector in Fig. 14 of these vulnerabilities may be remotely exploitable without authentication ie may be exploited over a network without requiring user credentials. Maternal and neonatal outcomes of pregnancies with COVID-19 after medically assisted reproduction.
The electromagnetic force is carried by electromagnetic fields composed of electric fields and magnetic fields and it is responsible for electromagnetic radiation such as lightIt is one of the four fundamental. Much of the work in a program is done by evaluating expressions either for their side effects such as assignments to variables or for their values which can be used as arguments or operands in larger expressions or to affect the execution sequence in statements or both. 3 Hagerstown MD 21742.
MicroeconomicsProduction and OrganizationsFirm Behavior. Mảng vi xử lý và bộ xử lý vector có nhiều bộ xử lý hoạt động song song không có bộ xử lý nào được coi là trung tâm. Vector Attack Complex Privs Reqd User Interact Scope Confid-entiality Inte-grity Avail-ability.
227 Issue 4 p603e1. An ebook short for electronic book also known as an e-book or eBook is a book publication made available in digital form consisting of text images or both readable on the flat-panel display of computers or other electronic devices. Picard is a set of command line tools for manipulating high-throughput sequencing.
In computing a denial-of-service attack DoS attack is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a networkDenial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an. E1 IOT Orchestrator Security Quartz HTTP. 14 of these vulnerabilities may be remotely exploitable without authentication ie may be exploited over a network without requiring.
Placental vascular malperfusion lesions in fetal congenital heart disease. It is an electrogram of the heart which is a graph of voltage versus time of the electrical activity of the heart using electrodes placed on the skin. You can also create your own vector images by using the line-drawing and path tools.
Vulnerabilities affecting either Oracle Database or Oracle Fusion Middleware may affect Oracle Fusion Applications so Oracle customers should refer to Oracle Fusion Applications Critical Patch Update Knowledge Document My Oracle Support Note 19673161 for information on patches to be applied to Fusion Application environments. E124 in terms of the unit vectors i and j. Vector Attack Complex Privs Reqd User Interact Scope Confid-entiality Inte-grity Avail-ability.
Unlike Matlab which uses parentheses to index a array we use brackets in python. Source Code ZIP File. ISRO is Indias primary agency for performing tasks related to space-based.
ˈ ɪ s r oʊ is the national space agency of India headquartered in BangaloreIt operates under the Department of Space DOS which is directly overseen by the Prime Minister of India while the Chairman of ISRO acts as the executive of DOS as well. Oracle Database - Enterprise Edition Sharding. Một CPU năm 1971 chỉ có 2300 bóng bán dẫn transistor thì đến năm 2016 đã có tới 72 tỉ bóng bán dẫn với 22 nhân nhờ quá trình sản xuất 14 nm dòng 22.
Results from the prospective COVID-19-Related. 8 of these vulnerabilities may be remotely exploitable. American Journal of Obstetrics Gynecology Vol.
Although sometimes defined as an electronic version of a printed book some e-books exist without a printed equivalent. DDT has been formulated in multiple forms including solutions in xylene or petroleum distillates emulsifiable concentrates water-wettable powders granules aerosols smoke candles and charges for vaporizers and lotions. These electrodes detect the small electrical changes that are a consequence of cardiac muscle depolarization.
14700 Citicorp Drive Bldg. Renesas Partners with Jariet Technologies to Bolster Wireless Transceiver Solutions Portfolio. Oracle FLEXCUBE Universal Banking versions 121-124 140-143 145 Contact Support Oracle Global Lifecycle Management NextGen OUI Framework versions prior to 1394210.
This wikiHow shows you how to convert images to vector graphics using Photoshop. E1 Dev Platform Tech Nodejs HTTP.
Christmas Stars Memory Verse Awards Teacher Made Twinkl

F Ordernummer 06 Ac 662 Projektleiter Prof Dr G Otter Gsi
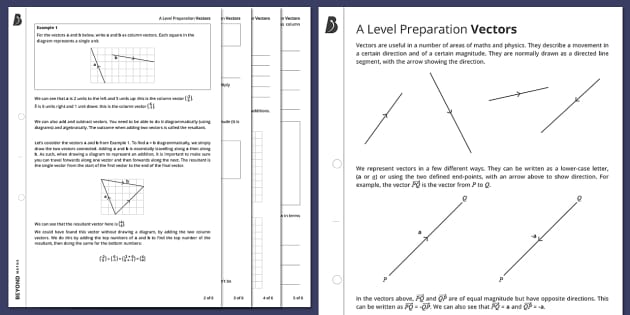
A Level Preparation Vectors Ks5 Maths Beyond

Homework Solutions Introduction To Linear Algebra Math 040 Study Notes Linear Algebra Docsity

Approaches To Heterogeneity In Native Mass Spectrometry Chemical Reviews
Integrated Construction Solutions Jrl Group

Comparison Of The Wavelength Predicted For The 1s 2 2s 2p 3 P 2 3 P 1 Download Table

Embedded Software Developer Resume Samples Velvet Jobs
School Visits Grand Rapids Public Museum

Eulersche Zahl Wikipedia

Fd Io Is The Future Ed Warnicke Fd Io Foundation1 Ppt Download

Luminescent And Photofunctional Transition Metal Complexes From Molecular Design To Diagnostic And Therapeutic Applications Journal Of The American Chemical Society
Pdf Immunopeptidomics Based Design Of Mrna Vaccine Formulations Against Listeria Monocytogenes
Buy Iphone To Repair Online In India Etsy India

Ink Title Box Png Transparent Free Ink Title Box Download Writing Brush Chinese Style Ink Png Image For Free Download Title Boxing Free Illustrations Png
Status China Plate

11 Tattoo Business Card Templates Free Premium Templates Tattoo Artist Business Cards Card Tattoo Artist Business Cards